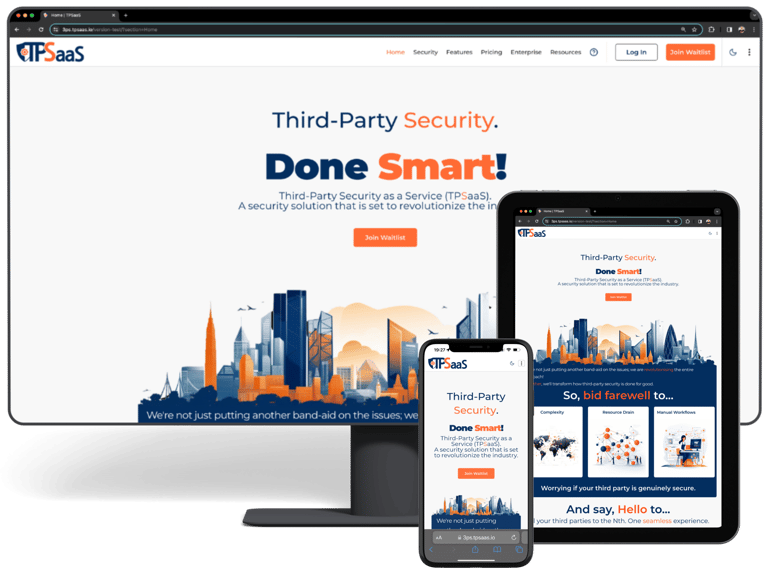
Third-Party Security Risk Management
Done Smart!
Third-Party Security as a Service (TPSaaS) is set to revolutionize how your third-parties are risk assessed.

We're not just putting another band-aid on the issues; we are revolutionising the entire approach!
Together, we'll transform how third-party security is done for good.
So, bid farewell to...
Complexity

Resource Drain

Manual Workflows

Worrying if your third party is genuinely secure.
And say, Hello to...
All your third parties to the Nth. One seamless experience across various industries, including InsurTech, RetailTech, EnergyTech, Tech/SaaS, FinTech, HealthTech, Telecommunications and beyond!
We understand the struggle.
Managing third-party security risks can be overwhelming, draining your time and resources. We get it; you're not alone. That is why we're here to help you with our secured SaaS solution to streamline and intelligently automate your Third-Party Risk Management, regardless of industry or regulation enabling you to focus on what truly matters— keeping your organisation secure and compliant without the hassle.

How to revolutionise your TPSRM?

Step 1
Click the'
'Button.

Step 2
Complete the information.

Step 3
Check your email.
The ROI extends beyond risk mitigation.
It includes operational efficiency and cost savings.

Marketplace
Our B2B marketplace offers a comprehensive solution for third-party risk management, compliance, quality assurance, and secure sourcing of third-party tech services.

Workflows
Automate tasks, improve collaboration, and enhance efficiency with streamlined workflows.

Risk & Tiering
Adaptive risk scoring segments vendors by criticality, focusing resources where they matter most to drive down mitigation costs and maximise security ROI.
The Threat Is Real.
Third-party data breaches up 49% YoY.

Most common third-party attacks 2023

Network Access
14%

40%
Third-Party Ransomware Attacks 2023

Ransomware
71%

27%
Time to Remediation 2023

Remediation
41%

50%
RAG/TLP — TPSaaS
Share of breaches involving third parties
InsurTech — 59%
GovTech — 58%
RetailTech — 52.4%
Tech / SaaS — 47.3%
EnergyTech — 46.7%
Telecommunications — 46% (proxy)
FinTech — 41.8%
HealthTech — 32.2%
Cross‑industry — 30%
Sources: Verizon DBIR 2025; SecurityScorecard 2025 sector reports; public reporting. Telecom shown as evidence‑based proxy.

Without unified cybersecurity efforts from both business and their suppliers, malicious actors will persistently target the weakest link.

—Vic du Toit - Founder
Your Defence Against the 49% Surge in Third-Party Breaches
TPSaaS secures your digital supply chain with continuous monitoring, built-in remediation, and audit-ready reporting from onboarding to offboarding.